RAD Insights


RAD Highlights

How RAD Security MCP Can Stop a Multi-Cluster Attack in Its Tracks
Stop multi-cluster Kubernetes attacks before they spread. See how RAD Security MCP gives teams cross-cluster visibility, context, and faster threat response.

How RAD Security MCP Can Stop a Multi-Cluster Attack in Its Tracks
Stop multi-cluster Kubernetes attacks before they spread. See how RAD Security MCP gives teams cross-cluster visibility, context, and faster threat response.

Fixing Security Issues Where They Happen: RAD + IDE via MCP
Fix cloud misconfigurations faster with RAD + Cursor. Use MCP to get AI-powered, in-IDE security fixes—no tool switching, just code-level remediation.

Fixing Security Issues Where They Happen: RAD + IDE via MCP
Fix cloud misconfigurations faster with RAD + Cursor. Use MCP to get AI-powered, in-IDE security fixes—no tool switching, just code-level remediation.

Securing Your Supply Chain: How RAD Security Detects the tj-actions/changed-files Attack
Learn how RAD Security detected the tj-actions/changed-files GitHub Action attack (CVE-2025-30066) and protected organizations from supply chain threats.

Securing Your Supply Chain: How RAD Security Detects the tj-actions/changed-files Attack
Learn how RAD Security detected the tj-actions/changed-files GitHub Action attack (CVE-2025-30066) and protected organizations from supply chain threats.

The Future of AI-Driven Cyber Defense Is Here—And We Just Raised $14M to Prove It
RAD Security announces series A to strengthen first AI-driven security platform for modern cloud and AI infrastructure.

The Future of AI-Driven Cyber Defense Is Here—And We Just Raised $14M to Prove It
RAD Security announces series A to strengthen first AI-driven security platform for modern cloud and AI infrastructure.
Latest Insights

Kubernetes Security Checklist: Cloud Native Security Basics Part VI
Kubernetes Security Checklist: Cloud Native Security Basics Part VI

Kubernetes Security Checklist: Cloud Native Security Basics Part VI
Kubernetes Security Checklist: Cloud Native Security Basics Part VI

Container Security: Cloud Native Security Basics Part II
Container Security: Cloud Native Security Basics Part II

Container Security: Cloud Native Security Basics Part II
Container Security: Cloud Native Security Basics Part II

Container Deployment: Cloud Native Security Basics Part III
Container Deployment: Cloud Native Security Basics Part III

Container Deployment: Cloud Native Security Basics Part III
Container Deployment: Cloud Native Security Basics Part III

DevOps, Deployment & Container Orchestration | Cloud Native Security Part I
DevOps, Deployment & Container Orchestration | Cloud Native Security Part I

DevOps, Deployment & Container Orchestration | Cloud Native Security Part I
DevOps, Deployment & Container Orchestration | Cloud Native Security Part I

Kubernetes RBAC: Role-Based Access Control
Kubernetes RBAC: Role-Based Access Control

Kubernetes RBAC: Role-Based Access Control
Kubernetes RBAC: Role-Based Access Control

FedRAMP Compliance Requirements for Enhancing SaaS Security
FedRAMP Compliance Requirements for Enhancing SaaS Security

FedRAMP Compliance Requirements for Enhancing SaaS Security
FedRAMP Compliance Requirements for Enhancing SaaS Security

ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response
ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response

ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response
ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response

What is Kubernetes Observability and Why it Matters in Cloud Native Security
What is Kubernetes Observability and Why it Matters in Cloud Native Security

What is Kubernetes Observability and Why it Matters in Cloud Native Security
What is Kubernetes Observability and Why it Matters in Cloud Native Security

Container Escape: Addressing the New runC and BuildKit Vulnerabilities
Container Escape: Addressing the New runC and BuildKit Vulnerabilities

Container Escape: Addressing the New runC and BuildKit Vulnerabilities
Container Escape: Addressing the New runC and BuildKit Vulnerabilities
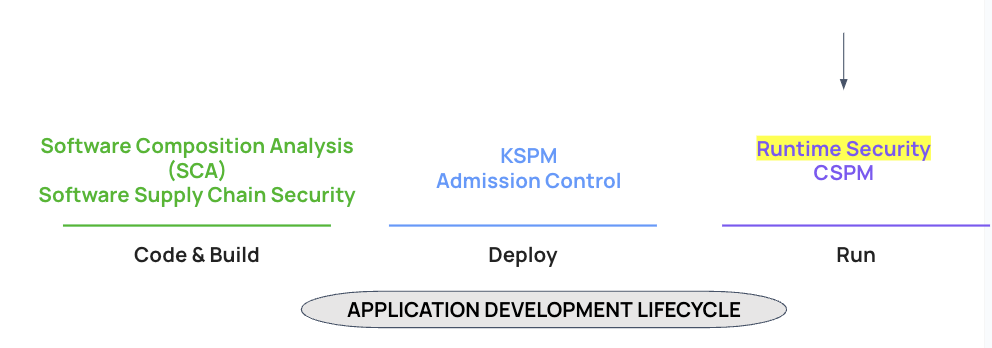
Best Practices for Container Runtime Security
Best Practices for Container Runtime Security

Best Practices for Container Runtime Security
Best Practices for Container Runtime Security

2024 Cloud Native Security Predictions
2024 Cloud Native Security Predictions

2024 Cloud Native Security Predictions
2024 Cloud Native Security Predictions


